Email authentication is a part of the email delivery process. To improve the success of email campaigns we recommend to authenticate your email using DKIM and SPF.
There are at least two reasons to use those protocols:
- Enhance your email reputation as sender. Each email sender has his own reputation which is generated by ISP. Many email providers use authentication to track sender reputation.
- Not to fall into spam. Over time email security standards become stronger and ISP work hard to get rid from spammers. ISPs use various forms of Email Authentication, knowing the owner of a domain that can provide list of mail sources that are “legitimate” and that they take responsibility for.
Mail-tester.com is an online tool that provides spam score and quality of your sent email and also gives advices how to improve your email deliverability rate.
There are few methods for email authentication. We will cover two of them:
- DKIM (DomainKeys Identified Mail) http://www.dkim.org
- SPF (Sender Policy Framework) http://www.openspf.org
SPF
SPF (Sender Policy Framework) is a text record in the DNS TXT-domain records. The record contains information about the list of servers that have the right to send a letter on behalf of the domain. Server from which mail is sent can provide a public list of approved senders
For example, SPF-record «example.com. TXT «v = spf1 + a + mx ~all» »says that send emails on behalf of« example.com domain “are the server specified in the A and MX-records of the domain, and mail sent from other servers should be deleted (Fail).
It is important to understand:
- SPF-record is not inherited to subdomains. For each of the third domain (or lower) level needs its own entry.
- SPF only checks HELO and MAIL FROM field.
How does SPF work?
Example of SPF DNS record
Be sure to replace xxx.xxx.xxx.xxx with your server’s IP address.
v=spf1 a mx ip4:xxx.xxx.xxx.xxx ~all
Every serious hosting provider should have guide the create this post. But in other case you can use these general instructions.
To add this record to your DNS records first you should login to your hosting control panel. Then navigate to DNS records management, usually under Domain Info Panel. Create new TXT record that looks like in the example and save it.
And that’s it.
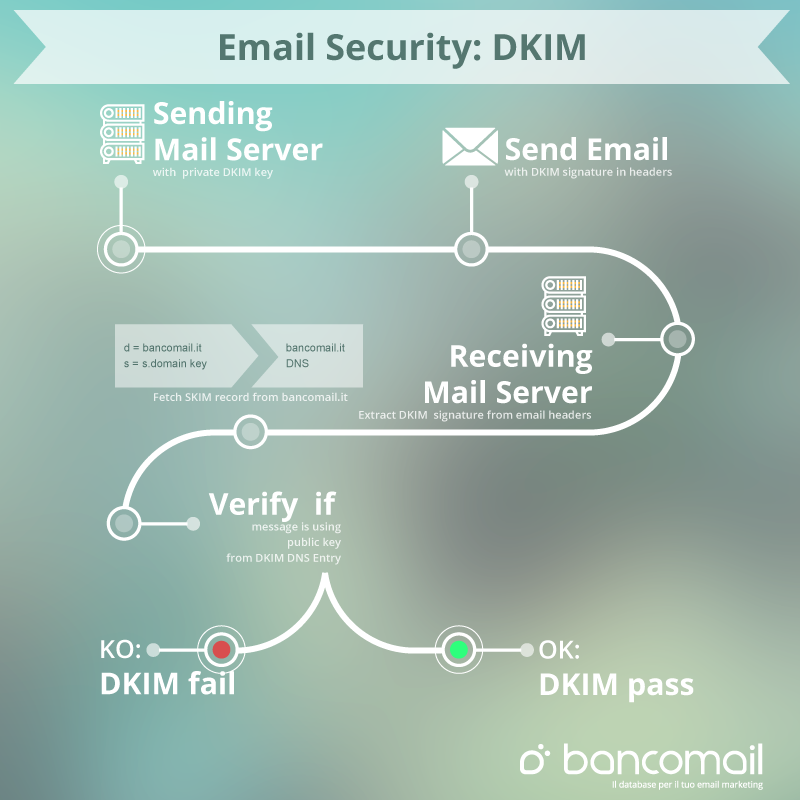
DKIM
DomainKeys Identified Mail or DKIM is the method for E-mail authentication and used to make sure email was not changed in transit between the sending and recipient servers.
Technology DKIM combines several existing antiphishing and antispam methods to improve the quality of the classification and identification of legitimate e-mail. Instead of the traditional IP-address, to determine the message sender DKIM adds a digital signature associated with the domain name of the organization. Text is automatically checked on the receiving end, then, to determine the reputation of the sender, used “white lists” and “black lists”.
The owner of the domain generates a private/public key pair which will be used to sign messages sent from that domain. The public key is placed in the DNS zone of the domain as a TXT record. The private key is kept on the mail server which is used as outgoing mail server for the domain.
When you send an email, the outgoing server will digitally sign it using your private key. The digital signature is added in the header in the sent email.
When your email is received, the recipient can then verify your DomainKeys signature using the public key in your domain’s DNS. If the signature matches, this means that you have validated both the sending domain and that the message has not been changed in transit.
How does DKIM work?
Example of DKIM DNS record
This site can help to create public and private keys passing domain name: http://dkimcore.org/tools/keys.html
We created example keys for domain example.com using the tool above.
Host name: default._domainkey.example.com
And the text correspond to public key:
1470929715.example._domainkey.example.com. IN TXT ( "v=DKIM1;t=s;p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDHuFmdB8fL6JR9MNImx9GicEeu" "Amv+/mBQlgDpHH+z9ELykiwdG/DvNBSgUXv3M4b0PrHgZsa69aUGAxK/Ejdu6XCu" "kt17ikt2I0GnGhkngaDhpgPJab0NwiF5vsOciQ+PkPhOiLUa4urHOhyO7RuYDECV" "5hVrp82ULlcgAUgMBwIDAQAB")
Normally most email sending services generates keys for you and you should only put them to DNS record.
Now you are protected!



 Buy email lists, when and why it’s convenient
Buy email lists, when and why it’s convenient How to choose the right platform for your Cold Email Marketing Campaign
How to choose the right platform for your Cold Email Marketing Campaign How to write a Cold Email that actually works
How to write a Cold Email that actually works